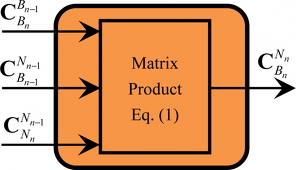
How to Promote Your ATI Course in Social Media LinkedIn for ATI Rocket Scientists Did you know that for 52% of professionals and executives, their LinkedIn profile is the #1 or #2 search result when someone searches on their name? For ATI instructors, that number is substantially lower – just 17%. One reason is […]
 How to Promote Your ATI Course in Social Media
LinkedIn for ATI Rocket Scientists
How to Promote Your ATI Course in Social Media
LinkedIn for ATI Rocket Scientists
Did you know that for 52% of professionals and executives, their LinkedIn profile is the #1 or #2 search result when someone searches on their name?
For ATI instructors, that number is substantially lower – just 17%. One reason is that about 25% of ATI instructors do not have a LinkedIn profile. Others have done so little with their profile that it isn’t included in the first page of search results.
If you are not using your LinkedIn profile, you are missing a huge opportunity. When people google you, your LinkedIn profile is likely the first place they go to learn about you. You have little control over what other information might be available on the web about you. But you have complete control over your LinkedIn profile. You can use your profile to tell your story – to give people the exact information you want them to have about your expertise and accomplishments.
Why not take advantage of that to promote your company, your services, and your course?

Here are some simple ways to promote your course using LinkedIn…
On Your LinkedIn Profile
Let’s start by talking about how to include your course on your LinkedIn profile so it is visible anytime someone googles you or visits your profile.
1. Add your role as an instructor.
Let people know that this course is one of the ways you share your knowledge. You can include your role as an instructor in several places on your profile:
- Experience – This is the equivalent of listing your role as a current job. (You can have more than one current job.) Use Applied Technology Institute as the employer. Make sure you drag and drop this role below your full-time position.
- Summary – Your summary is like a cover letter for your profile – use it to give people an overview of who you are and what you do. You can mention the type of training you do, along with the name of your course.
- Projects – The Projects section gives you an excellent way to share the course without giving it the same status as a full-time job.
- Headline – Your Headline comes directly below your name, at the top of your profile. You could add “ATI Instructor” at the end of your current Headline.
Start with an introduction, such as “I teach an intensive course through the Applied Technology Institute on [course title]” and copy/paste the description from your course materials or the ATI website. You can add a link to the course description on the ATI website.
This example from
Tom Logsdon’s profile, shows how you might phrase it:
Here are some other examples of instructors who include information about their courses on their LinkedIn profile:
- Buddy Wellborn – His Headline says “Instructor at ATI” and Buddy includes details about the course in his Experience section.
- D. Lee Fugal – Mentions the course in his Summary and Experience.
- Jim Jenkins – Courses are included throughout Jim’s profile, including his Headline, Summary, Experience, Projects, and Courses.
- 2. Link to your course page.
In the Contact Info section of your LinkedIn profile, you can link out to three websites. To add your course, go to Edit Profile, then click on Contact Info (just below your number of connections, next to a Rolodex card icon). Click on the pencil icon to the right of Websites to add a new site.
Choose the type of website you are adding. The best option is “Other:” as that allows you to insert your own name for the link. You have 35 characters – you can use a shortened version of your course title or simply “ATI Course.” Then copy/paste the link to the page about your course.
This example from Jim Jenkins’ profile shows how a customized link looks:
 3. Upload course materials.
3. Upload course materials.
You can upload course materials to help people better understand the content you cover. You could include PowerPoint presentations (from this course or other training), course handouts (PDFs), videos or graphics. They can be added to your Summary, Experience or Project. You can see an example of an upload above, in Tom Logsdon’s profile.
4. Add skills related to your course.
LinkedIn allows you to include up to 50 skills on your profile. If your current list of skills doesn’t include the topics you cover in your course, you might want to add them.
Go to the Skills & Endorsements section on your Edit Profile page, then click on Add skill. Start typing and let LinkedIn auto-complete your topic. If your exact topic isn’t included in the suggestions, you can add it.
5. Ask students for recommendations.
Are you still in touch with former students who were particularly appreciative of the training you provided in your course? You might want to ask them for a recommendation that you can include on your profile. Here are some tips on
asking for recommendations from LinkedIn expert Viveka Von Rosen.
6. Use an exciting background graphic.
You can add an image at the top of your profile – perhaps a photo of you teaching the course, a photo of your course materials, a graphic from your presentation, or simply some images related to your topic. You can see an example on
Val Traver’s profile.
Go to Edit Profile, then run your mouse over the top of the page (just above your name). You will see the option to Edit Background. Click there and upload your image. The ideal size is 1400 pixels by 425. LinkedIn prefers a JPG, PNG or GIF. Of course, only upload an image that you have permission to use.
Share News about Your Course
You can also use LinkedIn to attract more attendees to your course every time you teach.
7. When a course date is scheduled, share the news as a status update.
This lets your connections know that you are teaching a course – it’s a great way to reach the people who are most likely to be interested and able to make referrals.
Go to your LinkedIn home page, and click on the box under your photo that says “Share an update.” Copy and paste the URL of the page on the ATI website that has the course description. Once the section below populates with the ATI Courses logo and the course description, delete the URL. Replace it with a comment such as:
“Looking forward to teaching my next course on [title] for @Applied Technology Institute on [date] at [location].”
Note that when you finish typing “@Applied Technology Institute” it will give you the option to click on the company name. When you do that ATI will know you are promoting the course, and will be deeply grateful!
When people comment on your update, it’s nice to like their comment or reply with a “Thank you!” message. Their comment shares the update with their network, so they are giving your course publicity.
If you want to start doing more with status updates, here are some
good tips about what to share (and what not to share) from LinkedIn expert Kim Garst.
8. Share the news in LinkedIn Groups.
If you have joined any LinkedIn Groups in your areas of expertise, share the news there too.
Of course, in a Group you want to phrase the message a little differently. Instead of “Looking forward to teaching…” you might say “Registration is now open for…” or “For everyone interested in [topic], I’m teaching…”
You could also ask a thought-provoking question on one of the topics you cover. Here are some tips about
how to start an interesting discussion in a LinkedIn Group.
9. Post again if you still have seats available.
If the course date is getting close and you are looking for more people to register, you should post again. The text below will work as a status update and in most LinkedIn Groups.
“We still have several seats open for my course on [title] on [date] at [location]. If you know of anyone who might be interested, could you please forward this? Thanks. ”
“We have had a few last-minute cancellations for my course on [title] on [date] at [location]. Know anyone who might be interested in attending?”
10. Blog about the topic of the course.
When you publish blog posts on LinkedIn using their publishing platform, you get even more exposure than with a status update:
- The blog posts are pushed out to all your connections.
- They stay visible on your LinkedIn profile, and
- They are made available to Google and other search engines.
A blog post published on LinkedIn will rank higher than one posted elsewhere, because LinkedIn is such an authority site. So this can give your course considerable exposure.
You probably have written articles or have other content relevant to the course. Pick something that is 750-1500 words.
To publish it, go to your LinkedIn home page, and click on the link that says “Publish a post.” The interface is very simple – easier than using Microsoft Word. Include an image if you can. You probably have something in your training materials that will be perfect.
At the end of the post, add a sentence that says:
“To learn more, attend my course on [title].”
Link the title to the course description on the ATI website.
For more tips about blogging, you are welcome to join ProResource’s online training website. The
How to Write Blog Posts for LinkedIn course is free.
Take the first step
The most important version of your bio in the digital world is your LinkedIn summary. If you only make one change as a result of reading this blog post, it should be to add a strong summary to your LinkedIn profile. Write the summary promoting yourself as an expert in your field, not as a job seeker. Here are some resources that can help:
Write the first draft of your profile in a word processing program to spell-check and ensure you are within the required character counts. Then copy/paste it into the appropriate sections of your LinkedIn profile. You will have a stronger profile that tells your story effectively with just an hour or two of work!
Contributed by guest blogger Judy Schramm. Schramm is the CEO of ProResource, a marketing agency that works with thought leaders to help them create a powerful and effective presence in social media. ProResource offers done-for-you services as well as social media executive coaching. Contact Judy Schramm at
jschramm@proresource.com or 703-824-8482.
 How to Promote Your ATI Course in Social Media
LinkedIn for ATI Rocket Scientists
Did you know that for 52% of professionals and executives, their LinkedIn profile is the #1 or #2 search result when someone searches on their name?
For ATI instructors, that number is substantially lower – just 17%. One reason is that about 25% of ATI instructors do not have a LinkedIn profile. Others have done so little with their profile that it isn’t included in the first page of search results.
If you are not using your LinkedIn profile, you are missing a huge opportunity. When people google you, your LinkedIn profile is likely the first place they go to learn about you. You have little control over what other information might be available on the web about you. But you have complete control over your LinkedIn profile. You can use your profile to tell your story – to give people the exact information you want them to have about your expertise and accomplishments.
Why not take advantage of that to promote your company, your services, and your course?
How to Promote Your ATI Course in Social Media
LinkedIn for ATI Rocket Scientists
Did you know that for 52% of professionals and executives, their LinkedIn profile is the #1 or #2 search result when someone searches on their name?
For ATI instructors, that number is substantially lower – just 17%. One reason is that about 25% of ATI instructors do not have a LinkedIn profile. Others have done so little with their profile that it isn’t included in the first page of search results.
If you are not using your LinkedIn profile, you are missing a huge opportunity. When people google you, your LinkedIn profile is likely the first place they go to learn about you. You have little control over what other information might be available on the web about you. But you have complete control over your LinkedIn profile. You can use your profile to tell your story – to give people the exact information you want them to have about your expertise and accomplishments.
Why not take advantage of that to promote your company, your services, and your course?
 Here are some simple ways to promote your course using LinkedIn…
On Your LinkedIn Profile
Let’s start by talking about how to include your course on your LinkedIn profile so it is visible anytime someone googles you or visits your profile.
1. Add your role as an instructor.
Let people know that this course is one of the ways you share your knowledge. You can include your role as an instructor in several places on your profile:
Here are some simple ways to promote your course using LinkedIn…
On Your LinkedIn Profile
Let’s start by talking about how to include your course on your LinkedIn profile so it is visible anytime someone googles you or visits your profile.
1. Add your role as an instructor.
Let people know that this course is one of the ways you share your knowledge. You can include your role as an instructor in several places on your profile:
 3. Upload course materials.
You can upload course materials to help people better understand the content you cover. You could include PowerPoint presentations (from this course or other training), course handouts (PDFs), videos or graphics. They can be added to your Summary, Experience or Project. You can see an example of an upload above, in Tom Logsdon’s profile.
4. Add skills related to your course.
LinkedIn allows you to include up to 50 skills on your profile. If your current list of skills doesn’t include the topics you cover in your course, you might want to add them.
Go to the Skills & Endorsements section on your Edit Profile page, then click on Add skill. Start typing and let LinkedIn auto-complete your topic. If your exact topic isn’t included in the suggestions, you can add it.
5. Ask students for recommendations.
Are you still in touch with former students who were particularly appreciative of the training you provided in your course? You might want to ask them for a recommendation that you can include on your profile. Here are some tips on asking for recommendations from LinkedIn expert Viveka Von Rosen.
6. Use an exciting background graphic.
You can add an image at the top of your profile – perhaps a photo of you teaching the course, a photo of your course materials, a graphic from your presentation, or simply some images related to your topic. You can see an example on Val Traver’s profile.
Go to Edit Profile, then run your mouse over the top of the page (just above your name). You will see the option to Edit Background. Click there and upload your image. The ideal size is 1400 pixels by 425. LinkedIn prefers a JPG, PNG or GIF. Of course, only upload an image that you have permission to use.
Share News about Your Course
You can also use LinkedIn to attract more attendees to your course every time you teach.
7. When a course date is scheduled, share the news as a status update.
This lets your connections know that you are teaching a course – it’s a great way to reach the people who are most likely to be interested and able to make referrals.
Go to your LinkedIn home page, and click on the box under your photo that says “Share an update.” Copy and paste the URL of the page on the ATI website that has the course description. Once the section below populates with the ATI Courses logo and the course description, delete the URL. Replace it with a comment such as:
“Looking forward to teaching my next course on [title] for @Applied Technology Institute on [date] at [location].”
Note that when you finish typing “@Applied Technology Institute” it will give you the option to click on the company name. When you do that ATI will know you are promoting the course, and will be deeply grateful!
When people comment on your update, it’s nice to like their comment or reply with a “Thank you!” message. Their comment shares the update with their network, so they are giving your course publicity.
If you want to start doing more with status updates, here are some good tips about what to share (and what not to share) from LinkedIn expert Kim Garst.
8. Share the news in LinkedIn Groups.
If you have joined any LinkedIn Groups in your areas of expertise, share the news there too.
Of course, in a Group you want to phrase the message a little differently. Instead of “Looking forward to teaching…” you might say “Registration is now open for…” or “For everyone interested in [topic], I’m teaching…”
You could also ask a thought-provoking question on one of the topics you cover. Here are some tips about how to start an interesting discussion in a LinkedIn Group.
9. Post again if you still have seats available.
If the course date is getting close and you are looking for more people to register, you should post again. The text below will work as a status update and in most LinkedIn Groups.
“We still have several seats open for my course on [title] on [date] at [location]. If you know of anyone who might be interested, could you please forward this? Thanks. ”
“We have had a few last-minute cancellations for my course on [title] on [date] at [location]. Know anyone who might be interested in attending?”
10. Blog about the topic of the course.
When you publish blog posts on LinkedIn using their publishing platform, you get even more exposure than with a status update:
3. Upload course materials.
You can upload course materials to help people better understand the content you cover. You could include PowerPoint presentations (from this course or other training), course handouts (PDFs), videos or graphics. They can be added to your Summary, Experience or Project. You can see an example of an upload above, in Tom Logsdon’s profile.
4. Add skills related to your course.
LinkedIn allows you to include up to 50 skills on your profile. If your current list of skills doesn’t include the topics you cover in your course, you might want to add them.
Go to the Skills & Endorsements section on your Edit Profile page, then click on Add skill. Start typing and let LinkedIn auto-complete your topic. If your exact topic isn’t included in the suggestions, you can add it.
5. Ask students for recommendations.
Are you still in touch with former students who were particularly appreciative of the training you provided in your course? You might want to ask them for a recommendation that you can include on your profile. Here are some tips on asking for recommendations from LinkedIn expert Viveka Von Rosen.
6. Use an exciting background graphic.
You can add an image at the top of your profile – perhaps a photo of you teaching the course, a photo of your course materials, a graphic from your presentation, or simply some images related to your topic. You can see an example on Val Traver’s profile.
Go to Edit Profile, then run your mouse over the top of the page (just above your name). You will see the option to Edit Background. Click there and upload your image. The ideal size is 1400 pixels by 425. LinkedIn prefers a JPG, PNG or GIF. Of course, only upload an image that you have permission to use.
Share News about Your Course
You can also use LinkedIn to attract more attendees to your course every time you teach.
7. When a course date is scheduled, share the news as a status update.
This lets your connections know that you are teaching a course – it’s a great way to reach the people who are most likely to be interested and able to make referrals.
Go to your LinkedIn home page, and click on the box under your photo that says “Share an update.” Copy and paste the URL of the page on the ATI website that has the course description. Once the section below populates with the ATI Courses logo and the course description, delete the URL. Replace it with a comment such as:
“Looking forward to teaching my next course on [title] for @Applied Technology Institute on [date] at [location].”
Note that when you finish typing “@Applied Technology Institute” it will give you the option to click on the company name. When you do that ATI will know you are promoting the course, and will be deeply grateful!
When people comment on your update, it’s nice to like their comment or reply with a “Thank you!” message. Their comment shares the update with their network, so they are giving your course publicity.
If you want to start doing more with status updates, here are some good tips about what to share (and what not to share) from LinkedIn expert Kim Garst.
8. Share the news in LinkedIn Groups.
If you have joined any LinkedIn Groups in your areas of expertise, share the news there too.
Of course, in a Group you want to phrase the message a little differently. Instead of “Looking forward to teaching…” you might say “Registration is now open for…” or “For everyone interested in [topic], I’m teaching…”
You could also ask a thought-provoking question on one of the topics you cover. Here are some tips about how to start an interesting discussion in a LinkedIn Group.
9. Post again if you still have seats available.
If the course date is getting close and you are looking for more people to register, you should post again. The text below will work as a status update and in most LinkedIn Groups.
“We still have several seats open for my course on [title] on [date] at [location]. If you know of anyone who might be interested, could you please forward this? Thanks. ”
“We have had a few last-minute cancellations for my course on [title] on [date] at [location]. Know anyone who might be interested in attending?”
10. Blog about the topic of the course.
When you publish blog posts on LinkedIn using their publishing platform, you get even more exposure than with a status update:



 Dr. Menachem Levitas received his BS, maxima cum laude, from the University of Portland and his Ph.D. from the University of Virginia in 1975, both in physics. He has forty two years experience in science and engineering, thirty four of which in radar systems analysis, design, development, and testing for the Navy, Air Force, Marine Corps, and FAA. His experience encompasses many ground based, shipboard, and airborne radar systems. He has been technical lead on many radar efforts including Government source selection teams. He is the author of multiple radar based innovations and is a recipient of the Aegis Excellence Award for his contribution toward the AN/SPY-1 high range resolution (HRR) development. For many years, prior to his retirement in 2011, he had been the chief scientist of Technology Service Corporation / Washington. He continues to provide radar technical support under consulting agreements.
Dr. Menachem Levitas received his BS, maxima cum laude, from the University of Portland and his Ph.D. from the University of Virginia in 1975, both in physics. He has forty two years experience in science and engineering, thirty four of which in radar systems analysis, design, development, and testing for the Navy, Air Force, Marine Corps, and FAA. His experience encompasses many ground based, shipboard, and airborne radar systems. He has been technical lead on many radar efforts including Government source selection teams. He is the author of multiple radar based innovations and is a recipient of the Aegis Excellence Award for his contribution toward the AN/SPY-1 high range resolution (HRR) development. For many years, prior to his retirement in 2011, he had been the chief scientist of Technology Service Corporation / Washington. He continues to provide radar technical support under consulting agreements.
 The mystery of the missing Malaysia Airline flight MH370 is closer to being solved as authorities have revealed that they have tracked the final unexplained signal emitted by the jet, to the same point in the Indian Ocean, where the jet was believed to have crashed. Time will tell whether this is a definitive lead or a false alarm. We all hope it is the beginning to a successful answer.
Calling the latest development a promising lead, retired Air Chief Marshal Angus Houston, who is leading the search, said that an Australian navy ship had detected two sets of pulse signals that sounded just like an emergency locator beacon.
While the first set was heard on Saturday and lasted for two hours and 20 minutes, the Ocean Shield ship then lost contact with the “pings” but turned around and later heard further signals for 13 minutes, the Sydney Morning Herald reported.
However, the ship lost contact again and has been trying to relocate the signals.
Houston said that in the search so far it is probably the best information that the team has had, adding that the search team is encouraged that it is very close to where it needs to be.
He added that he would want more confirmation before he could say ‘this is it’.
Here is a list of the equipment that is being employed by the searchers.
If you find this information useful, please mention
The mystery of the missing Malaysia Airline flight MH370 is closer to being solved as authorities have revealed that they have tracked the final unexplained signal emitted by the jet, to the same point in the Indian Ocean, where the jet was believed to have crashed. Time will tell whether this is a definitive lead or a false alarm. We all hope it is the beginning to a successful answer.
Calling the latest development a promising lead, retired Air Chief Marshal Angus Houston, who is leading the search, said that an Australian navy ship had detected two sets of pulse signals that sounded just like an emergency locator beacon.
While the first set was heard on Saturday and lasted for two hours and 20 minutes, the Ocean Shield ship then lost contact with the “pings” but turned around and later heard further signals for 13 minutes, the Sydney Morning Herald reported.
However, the ship lost contact again and has been trying to relocate the signals.
Houston said that in the search so far it is probably the best information that the team has had, adding that the search team is encouraged that it is very close to where it needs to be.
He added that he would want more confirmation before he could say ‘this is it’.
Here is a list of the equipment that is being employed by the searchers.
If you find this information useful, please mention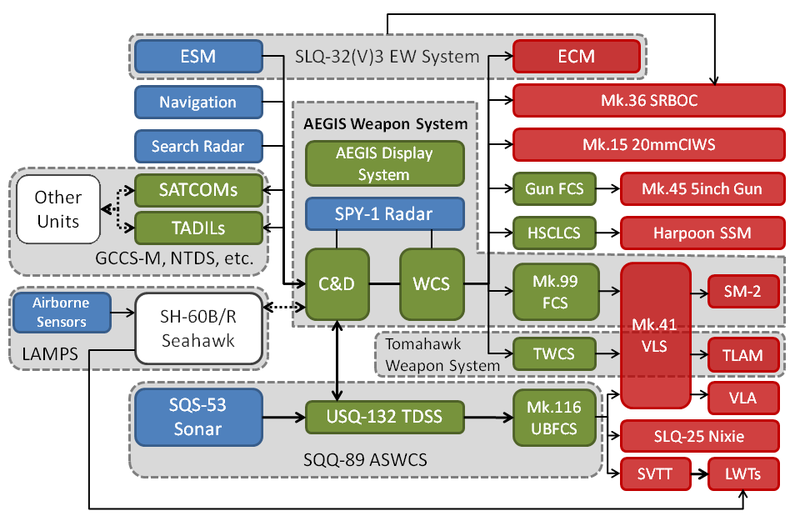

 The rise of Unmanned Aerial Vehicles (UAVs) is driving the development on unmanned technologies in other areas. Unmanned aerial vehicles (
The rise of Unmanned Aerial Vehicles (UAVs) is driving the development on unmanned technologies in other areas. Unmanned aerial vehicles ( Applied Technology Institute (ATICourses) offers
Applied Technology Institute (ATICourses) offers  ATI offers
ATI offers