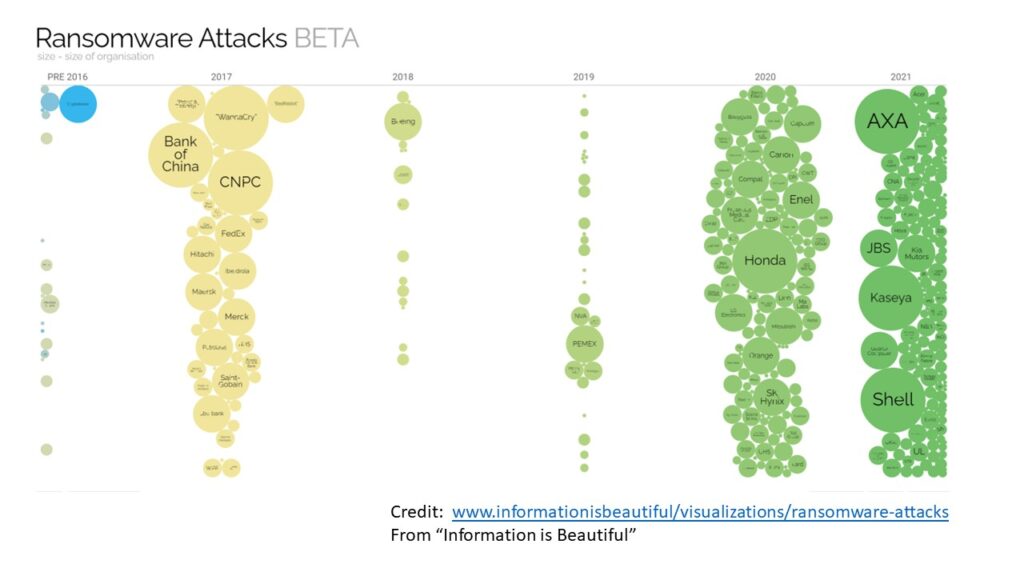
Anyone who reads the news knows that Ransomware attacks have become very popular among hackers, and very unpopular among victims.
In a Ransomware attack, the hacker penetrates your system and encrypts all of your files. So, you still have all your data; you simply have no way to access that data. You may just as well not even have your data. The hacker is looking for a ransom, and will only provide the encryption key if you pay him the money he demands. As seen in graphic below from “Information is Beautiful”, these attacks slowed down in 2018 and 2019, but are once again popular in 2020 and 2021.
Unfortunately, when dealing with ransomware hackers, you run the risk that he will take your money and not provide the key. Additionally, you run the risk that he will provide a key that works, but will repenetrate your system and demand a new ransom in the future. For the sake of your business, it is best to not get attacked in this manner. That’s easy to say, but how do you do that?
Protecting against Ransomware attacks is just one of the many things you will learn at an upcoming ATI course Cybersecurity Foundations in November 2022. This three-day course provides an overview of cybersecurity principles and mechanisms and highlights the challenges of protecting computing systems from determined adversaries. The course provides an understanding of the foundational elements of information security. It also gives the student an awareness of the current threat environment and architectures, mechanisms and technologies used to contain constrain, and control adversarial actions.
Take a look at the course description here, and if it looks like a course you may be interested in, please register for the class at that same site.
And, as always, if you want to see the full set of courses offered at ATI, please visit us at www.aticourses.com.